Cypherpunks write code. We know that someone has to write software to defend privacy, and we're going to write it.
— Eric Hughes
The Cypherpunk's Manifesto, 1993
In 1992, three Bay Area computer scientists launched a new mailing list for discussing cryptography, mathematics, politics, and philosophy. They called the members of this mailing list the cypherpunks: a portmanteau of cyberpunk, a genre of dystopian sci-fi, and ciphers, a staple of cryptography.
The cypherpunks were an eclectic crew, but they all shared a core conviction: that the Internet would soon become an important battleground for human freedom.
Rebels with a cause
Back in the early 90s, cyberspace was still the domain of hobbyists and hackers. But the cypherpunks believed that it was only a matter of time before the Internet would become central to society. Once governments understood the Internet's importance, they would move to co-opt, monitor, and censor it.

Long before Facebook, long before the Great Firewall of China, long before the Snowden revelations, the cypherpunks saw it coming. They foretold a regime of online censorship and surveillance that would eclipse the open Internet. And according to the cypherpunks, there was only one tool that could ensure the Internet's freedom: cryptography.
Cryptography is the mathematics of codes and codebreaking. Prior to the 1970s, cryptography was a relatively arcane field, practiced only by the military and by spy agencies. At the time, strong encryption (anything more than 40 bits of security) was considered to be a military munition and therefore illegal to export from the US.
But the cypherpunks believed cryptography was critical to a sovereign Internet. The inventions of Diffie-Hellman, RSA, and PGP presaged an age when individuals could have true freedom and privacy in their digital speech. Encryption was the best way to wrest power away from governments back toward individuals.
An early cypherpunk named Adam Back (who we'll be visiting again in this course) made his email signature the RSA encryption algorithm, written in five lines of Perl. Due to restrictions on the export of encryption algorithms, this was an illegal act of civil disobedience. He encouraged others on the mailing list to copy it in in solidarity.
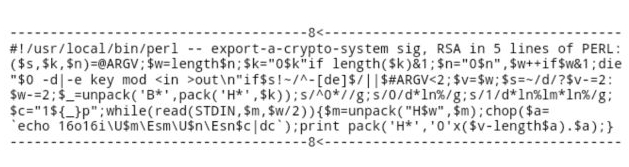
Over time, the combination of legal victories by people like Peter Junger, Phil Zimmerman, and Daniel Bernstein, the development of SSL and HTTPS by companies like Netscape, the practical availability of encryption software outside the US, and the degree to which lack of encryption was hampering e-commerce ended up winning the argument. Internet advocates won the First Crypto Wars, as export controls on encryption were liberalized.
But the cypherpunks knew that encryption alone would not be enough to liberate cyberspace. To build a truly free digital commons, you needed a completely sovereign economy. In other words, you needed a digitally native form of money.
Cypherpunk economics
It's important to understand the cypherpunk take on economic philosophy. The cypherpunks were deeply suspicious of central banks and their control over monetary policy after the end of Bretton Woods. Many years later, their suspicions were arguably justified after the financial crisis of 2008, when central banks created massive amounts of money to bail out failing banks.
It's worth taking a brief excursion here. In general, governments have two ways to finance their operations.
The first is taxation, where a government directly transfers money from citizens into its coffers. The second way is by printing money, traditionally known as seigniorage, which also transfers money to the government, but is a little more subtle to analyze. When a government prints money, the government obviously acquires currency, but citizens often find that the value of their currency holdings has depreciated, since there's now more money chasing the same set of real assets.
Taxation and seigniorage are roughly economically equivalent, but taxation generally requires the assent of citizens, whereas printing money can be done unilaterally. The cypherpunks thus saw money printing as a form of theft from the holders of currency.
The cypherpunks believed that to have a form of money truly native to cyberspace, it would have to be free from government intervention. After all, the Internet itself was already borderless and international! An Internet-native currency ought to put everyone, regardless of nationality, on a level playing field. Tying a digital economy to a singular fiat currency would subjugate it to the whims of a single country's central bank.
Furthermore, such a system should not have a central party capable of surveilling it. Otherwise that central party would be tempted to censor the system or manipulate the currency. After witnessing the many financial crises and hyperinflations in the 20th century, the cypherpunks believed that the soundest economic system was one that no one could manipulate.
Thus, cyberspace could not be truly free unless it had its own form of money. This they could agree on. But creating digital money had a technical problem that no one had yet been able to crack: the double spend problem.
The double spend problem
The double spend problem is easy to understand in principle. Imagine I have a digital $10 bill.
If that $10 bill is entirely digital, then it's just a bunch of bits on my hard drive. What's to stop me from copy and pasting those bits so I now have two $10 bills? And if I pay two people with copies of that $10 bill, how could they know which one is the "real" one?
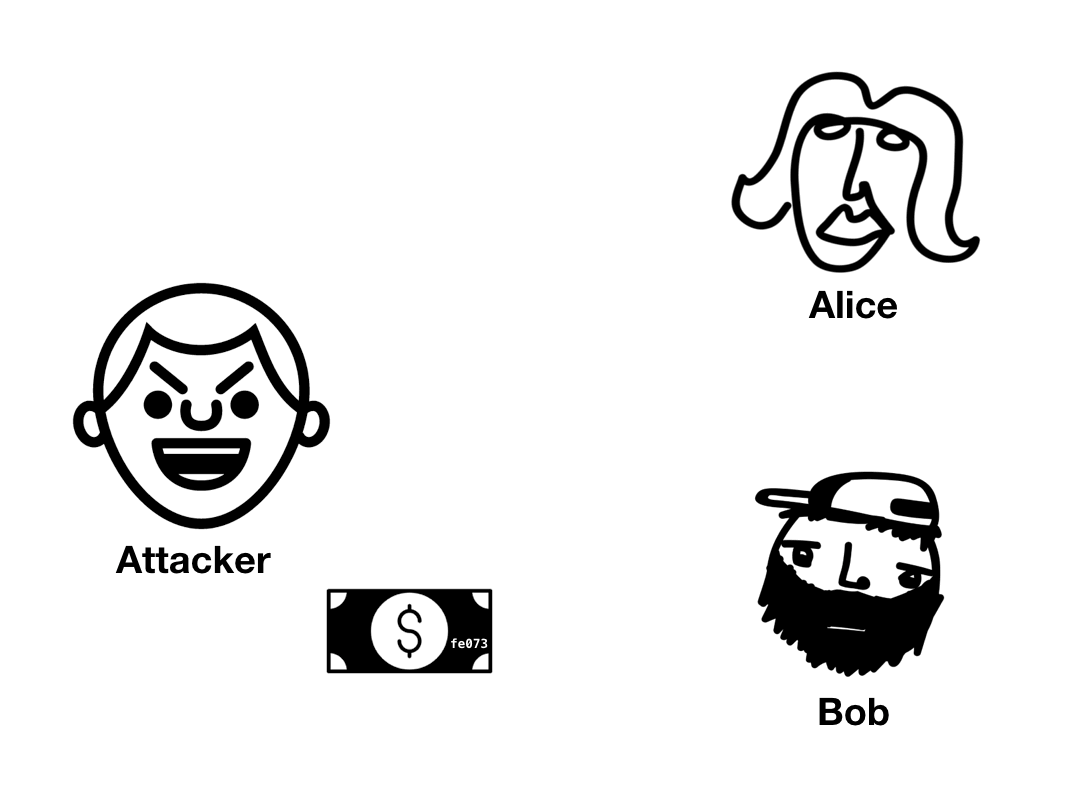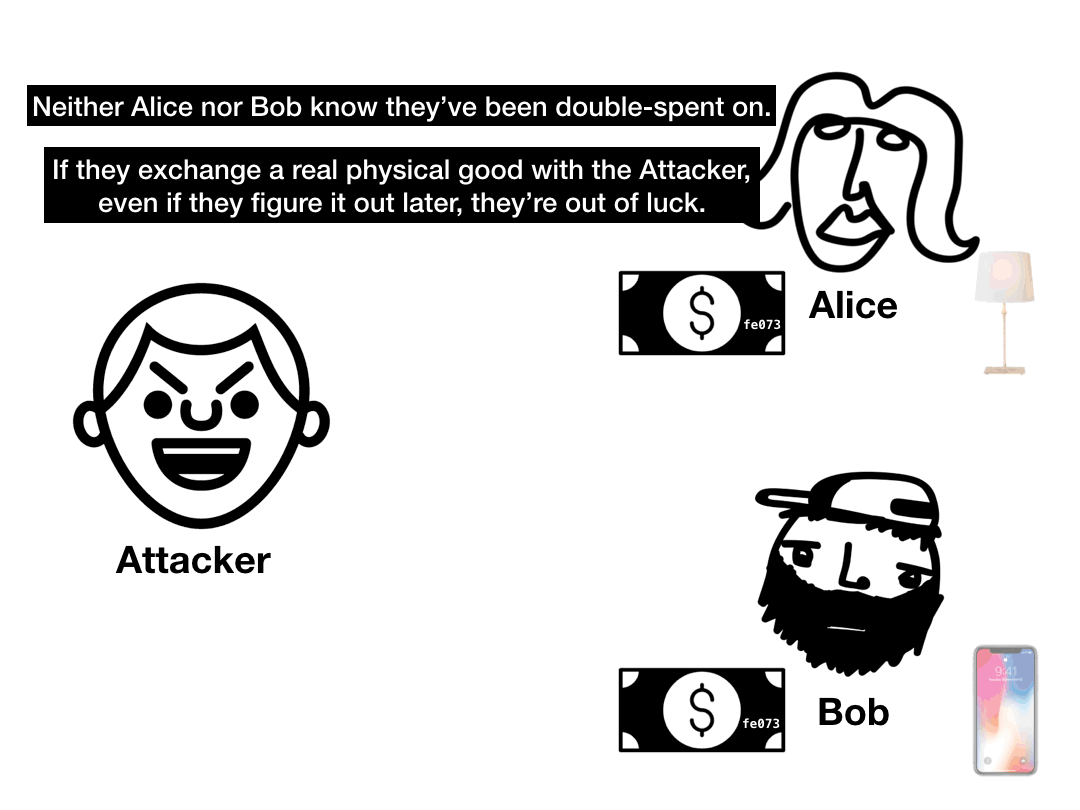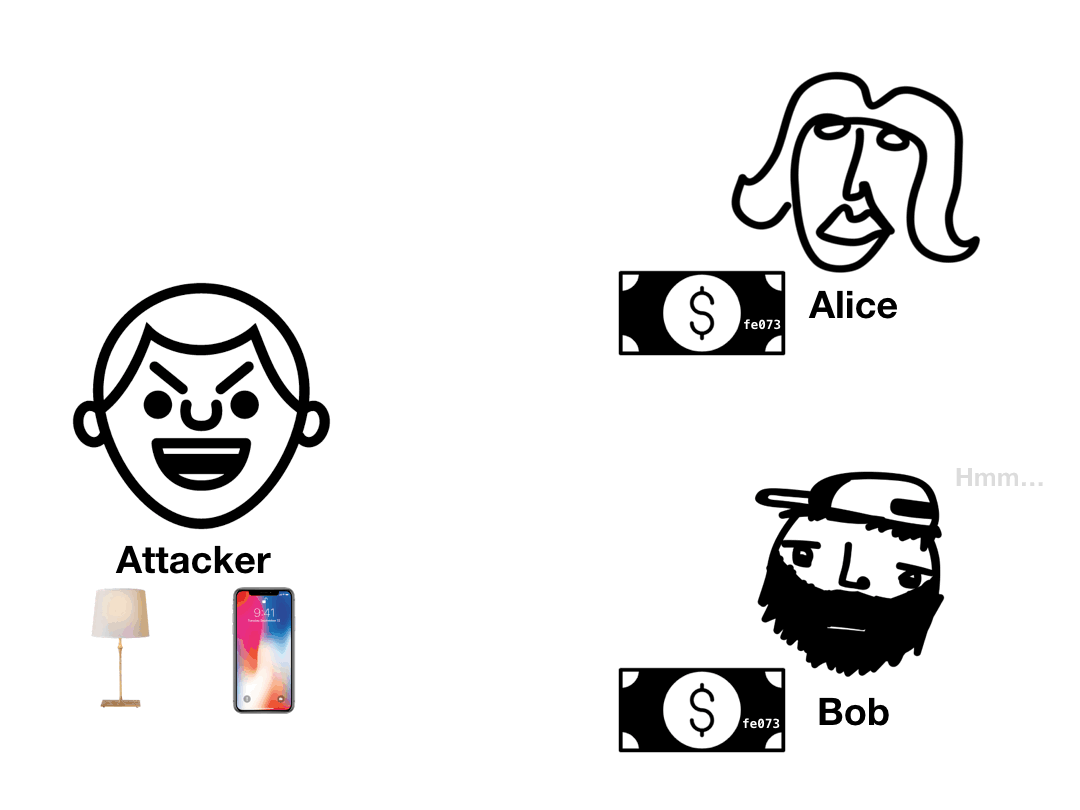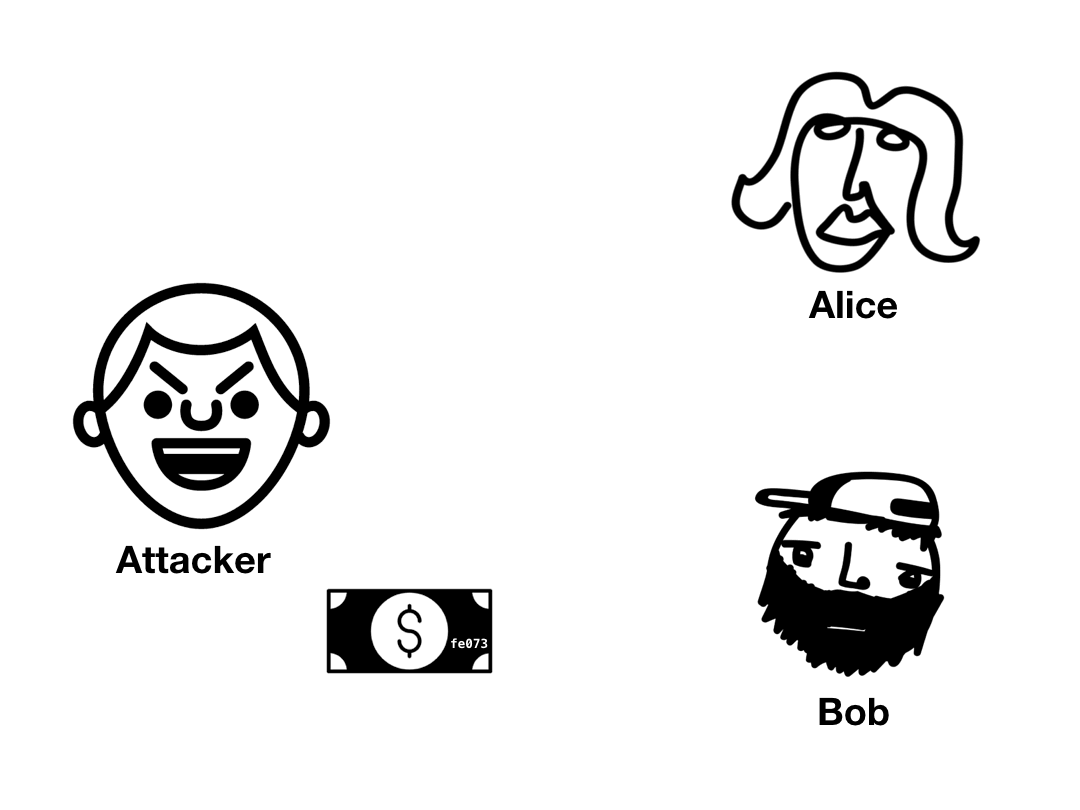
Fundamentally, the double spend problem can be conceived of as a counterfeiting problem. But the notion of counterfeiting only makes sense when there's a physical bill in the first place. In the digital world, a bill is just information. The "real bill" is just a sequence of bytes.
How is this problem solved with digital payments schemes like PayPal? Simple: PayPal's servers enforce the "anti-counterfeiting." PayPal has a single unified database that moves around its bytes—as a user, you don't get direct access to it. This protects the system from double spending, but at the expense of giving PayPal complete control over the monetary system. PayPal's intellectual descendants include the entire fintech industry today, including Square (founded in 2009) and Stripe (founded in 2011), all of which began with a centralized database at their core.
But if you could solve the double spend problem without relying on a trusted third party, you could potentially create a digital currency native to the Internet.
Was this possible? No one was sure.
So the cypherpunks got to work.
Chaumian eCash
David Chaum is considered by many to be the father of the cypherpunk movement. A prolific academic researcher, Chaum single-handedly created the field of anonymous communications research and invented many cryptographic protocols, including group signatures, mix networks, and blind signatures.

In 1990, David Chaum spearheaded the first serious attempt at building private digital money: DigiCash.
DigiCash used novel cryptography to ensure user privacy while solving the double spend problem. The underlying algorithm was known as eCash, first published in 1982 and later improved by other cryptographers.
What follows is a simplified description of the eCash algorithm:
- First, coins are issued to users by a bank. Each coin has a specific denomination and serial number, which are cryptographically signed by the bank.
- When a merchant receives a coin from a user, the merchant relays the coin to the issuing bank.
- The bank verifies that the signature over the denomination and serial number is valid and whether the coin has been previously spent. If these check out, the bank ensures that all spent coins are real and haven't been spent before. The merchant is then paid out for whatever the coins were worth.
On the face, this setup solves the double spend problem, but it seems quite centralized given the presence of the bank. And how does this achieve privacy? Well, there's a little extra cryptographic magic for that.
Say a user, Alice, deposits $5 into her bank. Alice then asks her bank to issue an eCash $5 bill for her to download. Accompanying this request she generates a random serial number for the new bill she's creating, plus a random "blinding factor". This blinding factor will be used to obfuscate which serial number belongs to her. The bank cryptographically signs the serial_number * blinding_factor coin, using what is known as a blind signature.
The blind signature scheme lets Alice remove the blinding factor, while still having a valid signature on the coin. In other words, the eCash issuer cannot track the blinded coins they signed. All they can see is the random unblinded serial numbers they eventually verify for merchants. And all the issuer is able to track are the total number of coins in each denomination and whether particular serial numbers have already been spent.

Chaumian eCash was a major leap forward in digital currencies. But in 1998, the company founded on eCash (DigiCash) went bankrupt. It ultimately lost out in user adoption against credit cards and less private payments systems like PayPal. And of course, when the company liquidated, its entire cash ecosystem evaporated.
The cypherpunks saw this failure and realized that Chaumian eCash had another weakness that had previously gone underappreciated: it relied on a single company. If digital cash were to flourish, it would have to grow beyond dependence on any central party.
It would have to become decentralized.
Other attempts
DigiCash was not the only attempt at creating a digital currency. The cypherpunks launched many experiments, including Mojo Nation, a payments system for incentivized file sharing, and Hashcash, a "payments" scheme for mitigating email spam. (We'll look at Hashcash and implement it ourselves in the cryptography module.)
But the cypherpunks weren't the only ones trying to create digital currencies. Founded in 1996, e-gold was one of the first dotcom companies to create a digital currency, two years before PayPal.
e-gold issued a digital currency backed by gold reserves that anyone could hold and transfer. At its height, e-gold processed more than $2B in transfers a year. It was immensely popular, but because it had few restrictions on signup, the currency was widely co-opted by hackers, scammers, and organized cybercriminals.
The US government took notice. After a lengthy court case, a court ruled e-gold guilty of money laundering and retroactive violations of money transmitter laws. The founder was found criminally liable, and in 2008, all e-gold balances were frozen. Over the next five years, the US government would manage redemptions of all e-gold account holders.
To the cypherpunks, e-gold demonstrated yet another important lesson: regulators did not want digital cash to exist.
The problem with collateral
While e-gold was collateralized with gold, DigiCash was collateralized with US dollars. But both ultimately fell within the purview of the state. If you wanted to create a currency that was beyond state control, it seemed that every form of collateral came with a centralization chokepoint.
So maybe, the cypherpunks thought, they should avoid collateral altogether.
Was it possible to create a non-collateralized form of money? The US dollar managed to pull it off after Bretton Woods and left behind the gold standard.
But if you had a non-collateralized form of money, you also somehow needed to enforce scarcity. Every form of money in the past, whether shells, gold, or US dollars, had some method of ensuring that the money supply didn't inflate out of control.
The cypherpunks explored several schemes for non-collateralized digital currencies. Two of the most important schemes were b-money, described by Wei Dai in 1998, and BitGold, described by Nick Szabo in 2005. Both schemes were designed by prominent cypherpunks and were strikingly similar to Bitcoin, but they were both missing key ingredients. We know that Satoshi was aware of b-money and he cited it in his whitepaper, and he later added an acknowledgement to BitGold on the Bitcoin website. It's worth briefly walking through their similarities and differences with Bitcoin, to get a sense of Bitcoin's lineage.
BitGold and b-money
- B-money and BitGold, like Bitcoin, use public key cryptography for identity.
- Both b-money and BitGold use proof-of-work to mint new coins. Bitcoin uses proof-of-work to also update the blockchain and append transactions.
- B-money and BitGold each use trusted timestamping servers for transaction ordering. Bitcoin implements a decentralized timestamping server via the "longest chain rule," as we'll discuss later.
- B-Money and BitGold achieved consensus by counting the total nodes in the network and letting the nodes vote. Bitcoin achieves consensus by counting the total work performed in the network.
B-Money and BitGold were ultimately both vulnerable to sybil attacks. A sybil attack is when a malicious user cheaply spins up many new "sybils" or identities, such as via a botnet. If the system has a simple majority vote rule, a dishonest attacker can easily overwhelm the system and determine the outcome of a vote. Any robust decentralized currency must be resistant to sybil attacks.
At the end of the day, b-money and BitGold were only described in blog posts, so they were relatively underspecified. They both would have required significant changes to be workable protocols and neither had working code. As such, they mostly traded in the arena of theoretical proposals. But these two designs would ultimately influence the digital currency that would see the light of day—Bitcoin.
It was ultimately the cypherpunks who laid the groundwork for the creation of something like Bitcoin. In the next section and the last chapter on the history of Bitcoin, we'll look at how Bitcoin was announced to the world, how it was received, and what we know about its mysterious cypherpunk creator, Satoshi Nakamoto.
Assignment
Click here to go to the quiz. Once you've completed it, you're ready to move on.
Additional Reading
- A Cypherpunk's Manifesto by Eric Hughes (1993)
- b-money by Wei Dai (1998)
- Bit Gold by Nick Szabo (2005)




